Owasp Top 10 2019 Web App Vulnerabilities
Lack of Device Management We havent solved this for non-IoT environments yet. The technical impact is severe.
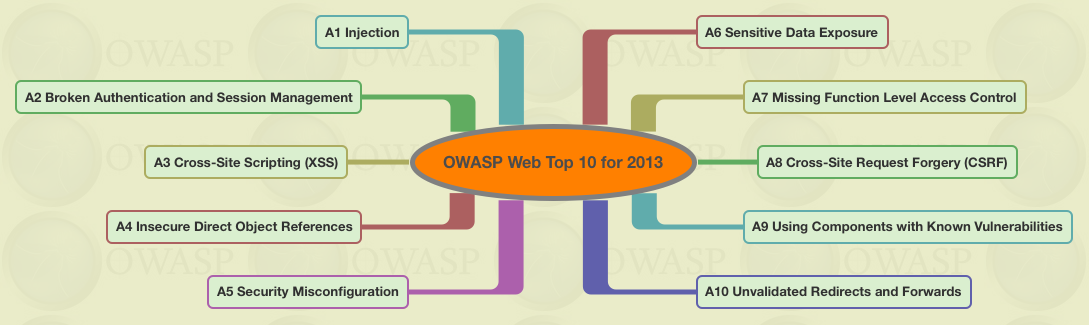
Owasp Top 10 Web App Vulnerabilities Over Time By Seralahthan Medium
Welcome to the OWASP Top 10 - 2021.
. Follow us here for an update as soon as OWASP Top Ten 2021 officially drops. One out of every five tested applications contained vulnerabilities allowing the hackers to attack a user session such as sensitive cookies without the HttpOnly and Secure. Like injection broken authentication has not changed position in the OWASP top 10 vulnerability list since 2013.
A misconfigured authentication system could allow attackers to impersonate legitimate users by compromising passwords session tokens etc. It also shows their risks impacts and countermeasures. OWASP API Security Top 10 2019 pt-BR translation release.
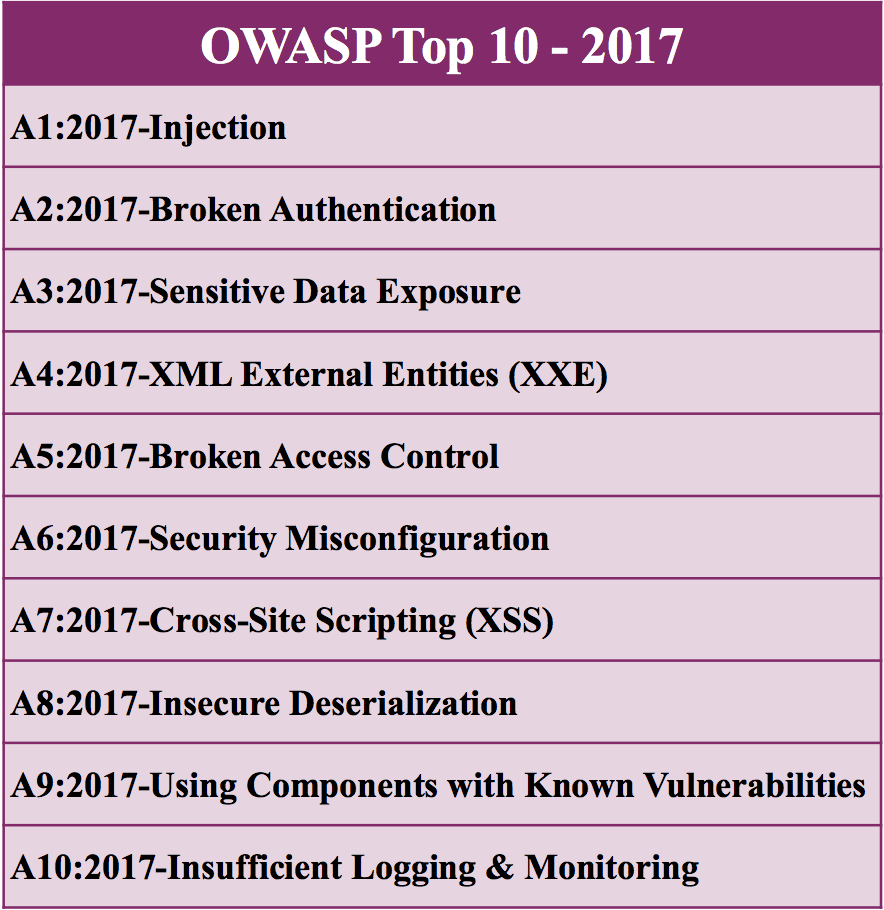
Sensitive data exposure 4. Updated every three to four years the latest OWASP vulnerabilities list was released in 2017. Insufficient Logging and Monitoring 3 4 5 8 9 11 13 15 16 17 2019 Sucuri.
OWASP top 10 is the list of top 10 application vulnerabilities along with the risk impact and countermeasures. As of our post date OWASP recently closed its call for input. 1-Injection - Injection is a web application vulnerability in which attacker tries to inject malicious code string in the form of input fields of web applications like forms comment.
OWASP Top 10 Vulnerabilities. Ultimately the OWASP Top 10 is the industry standard and needs to be prioritized when deploying any web or mobile app. The Open Web Application Security Project OWASP is an online community that produces freely-available articles methodologies documentation tools and technologies in the field of web application security.
The Open Web Application Security Project OWASP maintains a rating of the 10 most common threats. OWASP expects to complete the next major update of its Top Ten project sometime this year. With this Cross-Site Scripting weakness or XSS attackers could use web applications to send a.
The OWASP Top 10 for web applications includes. The list was last updated in 2017. B andwidth database connections disk storage CPU Memory Threads.
OWASP Top 10 is the list of the 10 most common application vulnerabilities. The report is based on a consensus among security experts from around the world. Injection occurs when an attacker exploits insecure code to insert or inject their own code into a program.
Broken Access control 6. When you try to put something thats too big into memory. The OWASP Top 10 2021 is all-new with a new graphic design and an available one-page infographic you can print or obtain from our home page.
And its considering a number of new contenders that have risen in prominence over the past 3-4 years. Answer-OWASP stands for Open Web Application Security ProjectIt is a public awareness document or list of top 10 most common application vulnerabilities which is released in every 4 years. A huge thank you to everyone that contributed their time and data for this iteration.
The SonarQube SAST engine analyzes your code for OWASP Top 10 vulnerabilities. Website security access controls should limit visitor access to only those pages or sections needed by that type of user. The OWASP Top 10 while not being an official standard is a widely acknowledged document used to classify vulnerability risks.
Limited resources can easily be the target. Welcome to the latest installment of the OWASP Top 10. Top 10 Security Risks Vulnerabilities Note.
Using Components with Known Vulnerabilities 10. In this section we explore each of these OWASP Top 10 vulnerabilities to better understand their impact and how they can be avoided. So what are the top 10 risks according to OWASP.
In no particular order heres our top 10 software vulnerability list for 2019. The list is usually refreshed in every 3-4 years. Adopting the OWASP Top 10 is perhaps the most effective first step towards changing your software development culture focused on producing secure code.
For each of the 10 threats in the list here is our take on the causes and. Buffer overflows are among the most well-known types of software vulnerabilities. A3- Cross-Site Scripting XSS Apparently it is the most common OWASP top 10 vulnerabilities and Fishery of Randomlands website had this one too.
Checks for known vulnerabilities in popular web applications such as. The RC of API Security Top-10 List was published during OWASP Global AppSec Amsterdam. XML External Entities XXE 5.
The OWASP Top 10 is a set of standards for common vulnerabilities and how to prevent them from becoming breaches for your company and users. The Top 10 OWASP vulnerabilities in 2021 are. Easy to generate a lot of load.
OWASP API Security Top 10 2019 pt-PT translation release. Lets dive into it. The Top 10 OWASP vulnerabilities are 1.
In particular they have published the OWASP Top 10 which describes in detail the major threats against web applications. The OWASP Top 10 is the reference standard for the most critical web application security risks. Most common OWASP Top 10 vulnerabilities percentage of web applications The most commonly encountered web application vulnerabilities in 2019 involved Security Misconfiguration.
OWASP Top 10 is an online document on OWASPs website that provides ranking of and remediation guidance for the top 10 most critical web application security risks. Automatically checks your web applications for XSS Cross-site Scripting SQL Injection other vulnerabilities. The same will be discussed along with a few examples which will help budding pentesters to help understand these vulnerabilities in applications and test the same.
Denial of Service - Description Web applications are susceptible to a denial of service because it is hard to detect the difference between ordinary traffic and an attack. Acunetix will scan your website for the OWASP Top 10 list of web security vulnerabilities complete with a comprehensive compliance report for the most recent OWASP Top 10 List of Risks. Cross-Site Scripting XSS 8.
The OWASP Top 10 a widely referenced document that lists the key threats to modern web applications hasnt changed much in the past few yearsBroken access controls cross-site scripting insecure configuration broken authentication these are some of the risks weve been constantly warned about since 2003. OWASP API Security Top 10 2019 stable version release. We break down each item its risk level how to test for them and how to resolve each.
OWASP Top 10 Vulnerabilities. 25 still rely on Excel spreadsheets to track assets 56 verify asset location only once a year while 10-15. Ad Track your code security against standard OWASP SANS categories.

Percentage Of Web Resources Affected By Owasp Top 10 Vulnerabilities Download Scientific Diagram

Owasp Top 10 Vulnerabilities Application Attacks Examples

The Owasp Top Ten What It Is And Isn T Cydrill Software Security
Comments
Post a Comment